1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
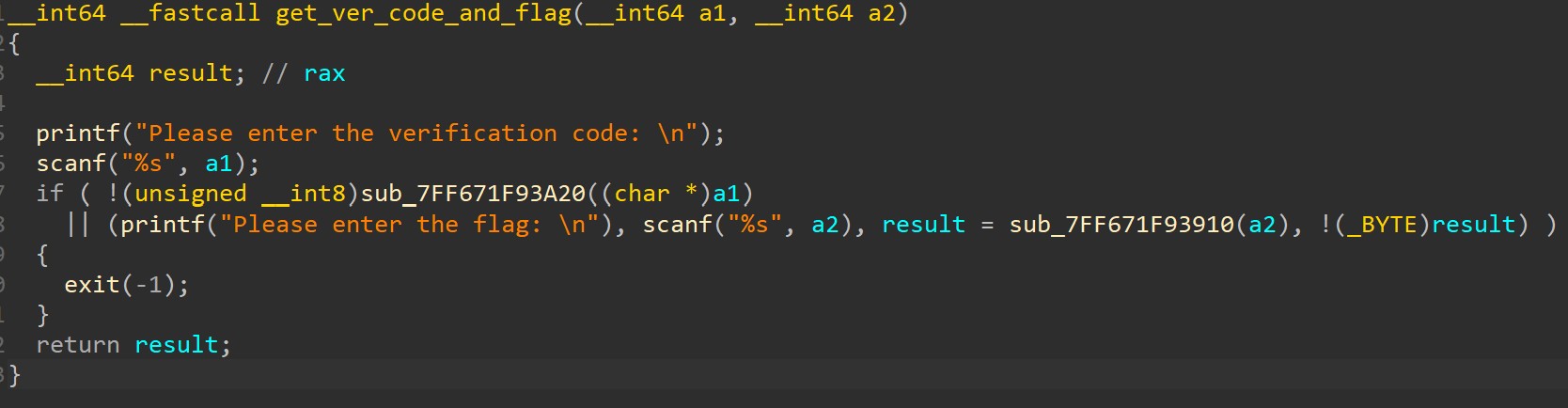
| from hashlib import md5
from pwn import *
table = string.printable
def hash(x):
m = md5()
m.update(x.encode())
return m.hexdigest()
maps = list(map(lambda x:hash(hash(x)), table))
flag = ['14d89c38cd0fb23a14be2798d449c182',
'a94837b18f8f43f29448b40a6e7386ba',
'af85d512594fc84a5c65ec9970956ea5',
'af85d512594fc84a5c65ec9970956ea5',
'10e21da237a4a1491e769df6f4c3b419',
'a705e8280082f93f07e3486636f3827a',
'297e7ca127d2eef674c119331fe30dff',
'b5d2099e49bdb07b8176dff5e23b3c14',
'83be264eb452fcf0a1c322f2c7cbf987',
'a94837b18f8f43f29448b40a6e7386ba',
'71b0438bf46aa26928c7f5a371d619e1',
'a705e8280082f93f07e3486636f3827a',
'ac49073a7165f41c57eb2c1806a7092e',
'a94837b18f8f43f29448b40a6e7386ba',
'af85d512594fc84a5c65ec9970956ea5',
'ed108f6919ebadc8e809f8b86ef40b05',
'10e21da237a4a1491e769df6f4c3b419',
'3cfd436919bc3107d68b912ee647f341',
'a705e8280082f93f07e3486636f3827a',
'65c162f7c43612ba1bdf4d0f2912bbc0',
'10e21da237a4a1491e769df6f4c3b419',
'a705e8280082f93f07e3486636f3827a',
'3cfd436919bc3107d68b912ee647f341',
'557460d317ae874c924e9be336a83cbe',
'a705e8280082f93f07e3486636f3827a',
'9203d8a26e241e63e4b35b3527440998',
'10e21da237a4a1491e769df6f4c3b419',
'f91b2663febba8a884487f7de5e1d249',
'a705e8280082f93f07e3486636f3827a',
'd7afde3e7059cd0a0fe09eec4b0008cd',
'488c428cd4a8d916deee7c1613c8b2fd',
'39abe4bca904bca5a11121955a2996bf',
'a705e8280082f93f07e3486636f3827a',
'3cfd436919bc3107d68b912ee647f341',
'39abe4bca904bca5a11121955a2996bf',
'4e44f1ac85cd60e3caa56bfd4afb675e',
'45cf8ddfae1d78741d8f1c622689e4af',
'3cfd436919bc3107d68b912ee647f341',
'39abe4bca904bca5a11121955a2996bf',
'4e44f1ac85cd60e3caa56bfd4afb675e',
'37327bb06c83cb29cefde1963ea588aa',
'a705e8280082f93f07e3486636f3827a',
'23e65a679105b85c5dc7034fded4fb5f',
'10e21da237a4a1491e769df6f4c3b419',
'71b0438bf46aa26928c7f5a371d619e1',
'af85d512594fc84a5c65ec9970956ea5',
'39abe4bca904bca5a11121955a2996bf']
f=""
for i in flag:
f+=table[maps.index(i)]
print(f)
|

Comments