题目质量还不错,断断续续做了一天,最后第9也还可以。
misc
问卷
填问卷
仔细找找
图片转成黑白,可以直接看到flag

vnctf{34aE@w}
Web
GameV4.0
源码data里找到flag
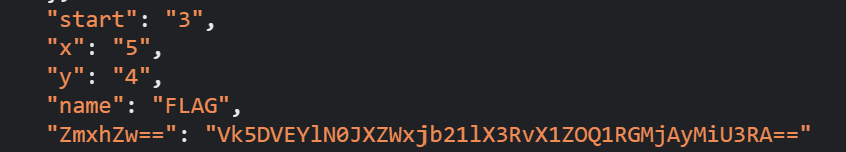
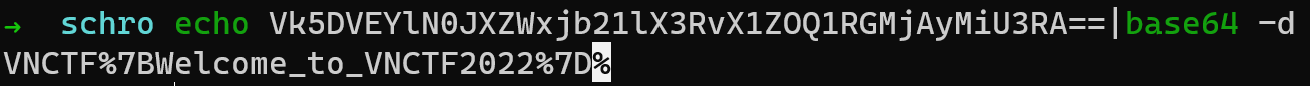
解一下base64得到flag
Crypto
ezmath
满足
$$
2^n-1\mod15=0
$$
只需要满足 n=4x
$$
2^{4x}-1\mod15=0
$$
$$
16^x-1\mod15=0
$$
$$
(15+1)^x-1\mod15=0
$$
$$
\Sigma_{k=0}^xC_x^k15^k-1\mod15=0
$$
$$
\Sigma_{k=1}^xC_x^k15^k\mod15=0
$$
满足要求,解析出来数字直接乘4就可以了
1 | from pwn import * |
re
BabyMaze
pyc文件,前面加花,直接反编译会卡死,去花可以反编译,但是程序不难,直接看也能很容易看懂
1 | 0 LOAD_CONST 1: 1 |
wasd移动,导出地图,发现地图很小没必要写深搜,走一遍就行了
1 | ans="ssssddssaassddddwwwwddwwddddddwwddddddssddwwddddddddssssaawwaassaassaassddssaassaawwwwwwaaaaaaaassaassddddwwddssddssssaassddssssaaaaaawwddwwaawwwwaassssssssssssddddssddssddddddddwwaaaaaawwwwddssddwwwwwwwwddssddssssssssddddss" |
cm狗
vm,简单解析一下指令看看程序是不是很复杂
1 | opcodes = [0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000057, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000065, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006C, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000063, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006F, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006D, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000065, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000020, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000074, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006F, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000020, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000056, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000004E, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000043, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000054, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000046, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000032, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000030, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000032, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000032, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000021, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000000A, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000069, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006E, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000070, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000075, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000074, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000020, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000066, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006C, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000061, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000067, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000003A, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000000A, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000013, 0x00000049, 0x00000001, 0x00000003, 0x00000000, 0x00000001, 0x00000001, 0x0000002B, 0x00000001, 0x00000002, 0x00000001, 0x00000061, 0x00000000, 0x00000000, 0x00000005, 0x00000000, 0x00000000, 0x00000008, 0x00000001, 0x00000002, 0x0000000E, 0x00000001, 0x00000003, 0x00000001, 0x00000000, 0x00000000, 0x00000005, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000006, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000006, 0x00000000, 0x00000002, 0x00000000, 0x00000006, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000006, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000006, 0x00000000, 0x00000002, 0x00000000, 0x00000006, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000006, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000006, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000007, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000007, 0x00000000, 0x00000002, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000007, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000007, 0x00000000, 0x00000002, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000007, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000007, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000008, 0x00000000, 0x00000002, 0x00000000, 0x00000008, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000008, 0x00000000, 0x00000002, 0x00000000, 0x00000008, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000008, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000009, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000009, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000009, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000009, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000009, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000009, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000A, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000002, 0x00000000, 0x0000000A, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000A, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000002, 0x00000000, 0x0000000A, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000A, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000B, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000B, 0x00000000, 0x00000002, 0x00000000, 0x0000000B, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000B, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000B, 0x00000000, 0x00000002, 0x00000000, 0x0000000B, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000B, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000B, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000C, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000C, 0x00000000, 0x00000002, 0x00000000, 0x0000000C, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000C, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000C, 0x00000000, 0x00000002, 0x00000000, 0x0000000C, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000C, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000C, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000D, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000D, 0x00000000, 0x00000002, 0x00000000, 0x0000000D, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000D, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000D, 0x00000000, 0x00000002, 0x00000000, 0x0000000D, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000D, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000D, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000E, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000E, 0x00000000, 0x00000002, 0x00000000, 0x0000000E, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000E, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000E, 0x00000000, 0x00000002, 0x00000000, 0x0000000E, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000E, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000E, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000F, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000F, 0x00000000, 0x00000002, 0x00000000, 0x0000000F, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000F, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000F, 0x00000000, 0x00000002, 0x00000000, 0x0000000F, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000F, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000F, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000010, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000010, 0x00000000, 0x00000002, 0x00000000, 0x00000010, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000010, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000010, 0x00000000, 0x00000002, 0x00000000, 0x00000010, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000010, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000010, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000005, 0x00000006, 0x00000000, 0x00000005, 0x00000007, 0x00000000, 0x00000005, 0x00000008, 0x00000000, 0x00000005, 0x00000009, 0x00000000, 0x00000005, 0x0000000A, 0x00000000, 0x00000005, 0x0000000B, 0x00000000, 0x00000005, 0x0000000C, 0x00000000, 0x00000005, 0x0000000D, 0x00000000, 0x00000005, 0x0000000E, 0x00000000, 0x00000005, 0x0000000F, 0x00000000, 0x00000005, 0x00000010, 0x00000000, 0x00000006, 0x00000001, 0x00000000, 0x00000006, 0x00000002, 0x00000000, 0x00000001, 0x00000014, 0x0000011C, 0x00000001, 0x00000000, 0x00000154, 0x0000000C, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0xE8D1D5DF, 0x00000001, 0x00000013, 0x00000183, 0x00000001, 0x00000014, 0x00000153, 0x0000000E, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0xF5E3C114, 0x0000000E, 0x00000002, 0x00000000, 0x00000006, 0x00000001, 0x00000000, 0x00000006, 0x00000002, 0x00000000, 0x00000001, 0x00000014, 0x00000127, 0x00000001, 0x00000000, 0x00000154, 0x0000000C, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x228EC216, 0x00000001, 0x00000013, 0x00000183, 0x00000001, 0x00000014, 0x00000153, 0x0000000E, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x89D45A61, 0x0000000E, 0x00000002, 0x00000000, 0x00000006, 0x00000001, 0x00000000, 0x00000006, 0x00000002, 0x00000000, 0x00000001, 0x00000014, 0x00000132, 0x00000001, 0x00000000, 0x00000154, 0x0000000C, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x655B8F69, 0x00000001, 0x00000013, 0x00000183, 0x00000001, 0x00000014, 0x00000153, 0x0000000E, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x2484A07A, 0x0000000E, 0x00000002, 0x00000000, 0x00000006, 0x00000001, 0x00000000, 0x00000006, 0x00000002, 0x00000000, 0x00000001, 0x00000014, 0x0000013D, 0x00000001, 0x00000000, 0x00000154, 0x0000000C, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0xD9E5E7F8, 0x00000001, 0x00000013, 0x00000183, 0x00000001, 0x00000014, 0x00000153, 0x0000000E, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x3A441532, 0x0000000E, 0x00000002, 0x00000000, 0x00000006, 0x00000001, 0x00000000, 0x00000006, 0x00000002, 0x00000000, 0x00000001, 0x00000014, 0x00000148, 0x00000001, 0x00000000, 0x00000154, 0x0000000C, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x91AB7E88, 0x00000001, 0x00000013, 0x00000183, 0x00000001, 0x00000014, 0x00000153, 0x0000000E, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x69FC64BC, 0x0000000E, 0x00000002, 0x00000000, 0x00000006, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x007D3765, 0x0000000E, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x00000189, 0x0000000C, 0x00000000, 0x00000000, 0x00000063, 0x00000000, 0x00000000, 0x00000001, 0x00000003, 0x9E3779B9, 0x00000001, 0x00000004, 0x00095C4C, 0x00000001, 0x00000005, 0x0000871D, 0x00000001, 0x00000006, 0x0001A7B7, 0x00000001, 0x00000007, 0x0012C7C7, 0x00000001, 0x00000008, 0x00000000, 0x00000001, 0x00000011, 0x00000010, 0x00000001, 0x00000012, 0x00000020, 0x00000001, 0x00000013, 0x00000160, 0x00000001, 0x0000000A, 0x00000000, 0x00000001, 0x0000000B, 0x00000020, 0x00000001, 0x0000000C, 0x00000001, 0x00000007, 0x00000008, 0x00000003, 0x00000002, 0x00000000, 0x00000002, 0x0000000A, 0x00000000, 0x00000011, 0x00000007, 0x00000000, 0x00000004, 0x00000002, 0x0000000E, 0x00000000, 0x00000002, 0x00000000, 0x00000002, 0x00000007, 0x00000000, 0x00000008, 0x00000002, 0x0000000F, 0x00000000, 0x00000002, 0x00000000, 0x00000002, 0x00000009, 0x00000000, 0x00000012, 0x00000007, 0x00000000, 0x00000005, 0x00000002, 0x00000010, 0x00000000, 0x00000002, 0x00000000, 0x0000000E, 0x0000000B, 0x00000000, 0x0000000F, 0x0000000B, 0x00000000, 0x00000010, 0x00000007, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000001, 0x0000000A, 0x00000000, 0x00000011, 0x00000007, 0x00000000, 0x00000006, 0x00000002, 0x0000000E, 0x00000000, 0x00000002, 0x00000000, 0x00000001, 0x00000007, 0x00000000, 0x00000008, 0x00000002, 0x0000000F, 0x00000000, 0x00000002, 0x00000000, 0x00000001, 0x00000009, 0x00000000, 0x00000012, 0x00000007, 0x00000000, 0x00000007, 0x00000002, 0x00000010, 0x00000000, 0x00000002, 0x00000000, 0x0000000E, 0x0000000B, 0x00000000, 0x0000000F, 0x0000000B, 0x00000000, 0x00000010, 0x00000007, 0x00000002, 0x00000000, 0x00000008, 0x0000000B, 0x0000000C, 0x0000000E, 0x0000000B, 0x0000000A, 0x0000000C, 0x00000014, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006E, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006F, 0x00000062, 0x00000000, 0x00000000, 0x0000000C, 0x00000014, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000079, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000065, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000073, 0x00000062, 0x00000000, 0x00000000, 0x0000000C, 0x00000014, 0x00000000] |
1 | 0 nop |
程序很简单,循环输入,每四个Byte按照小端序转换成DWORD,前10个DWORD进行tea加密,然后对比一下结果就行了
1 | #include <stdio.h> |
cm1
android,动态加载dex,主要的代码逻辑都在动态加载的dex里,直接运行然后把生成的classes.dex拷贝出来
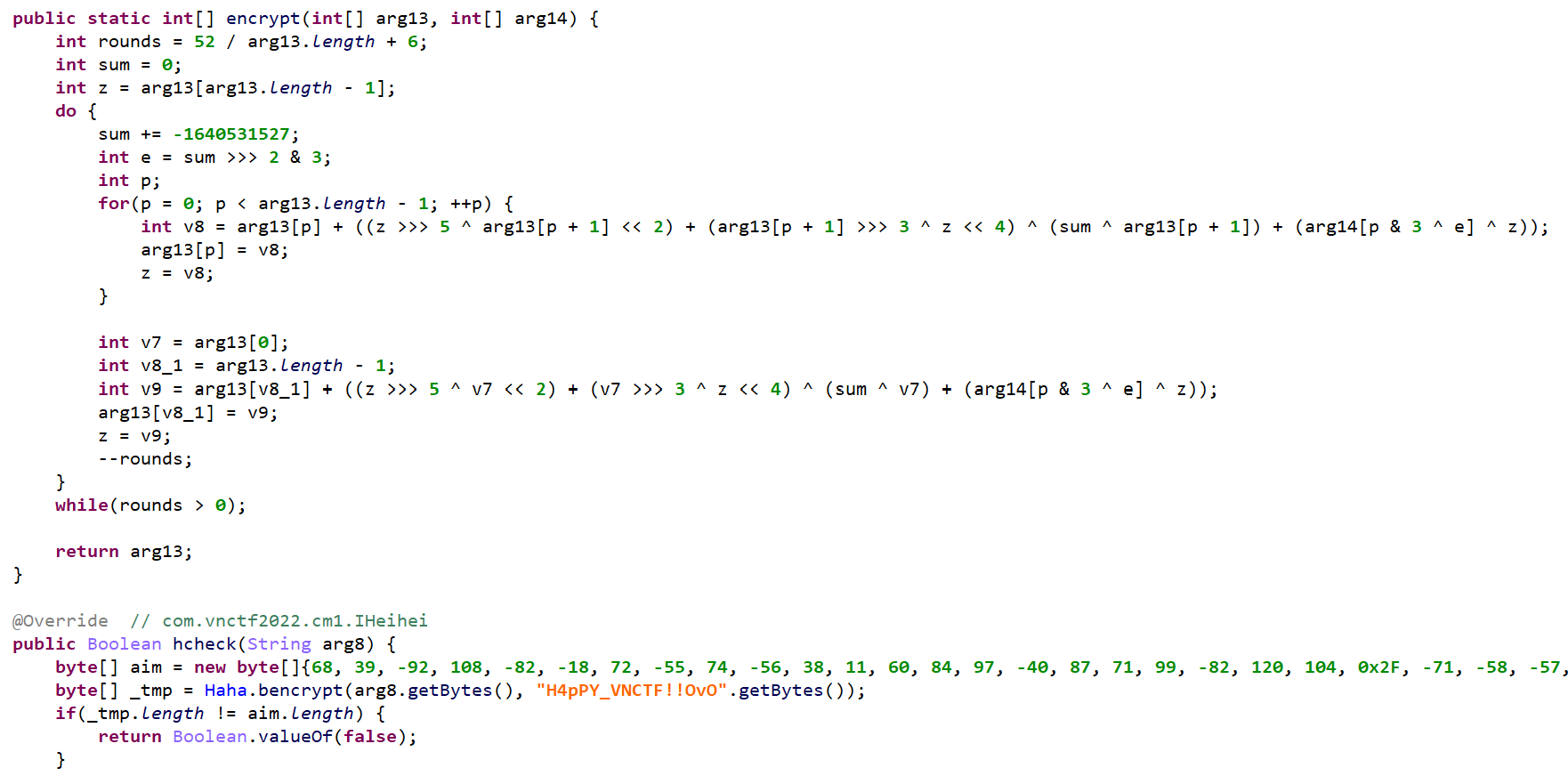
密文,密钥,加密方式都有,很明显是xxtea,写脚本直接解密
1 | #include <stdio.h> |
Comments