这次的赛制是第一次见到的沙漏赛制,对我这种不急不忙佛系做题的不是很友好,最后的名次也还行,前排观赏前面的神仙打架
签到
程序是python打包出来的,解包找到主程序checkin,补上pyc头文件,反编译得到python代码
1 | import cv2, re, sys |
看了一下代码,有OCR,发现真的和题目描述一样对着电脑摄像头扫“FUN”就可以了,然后放弃继续逆向写了个大大的FUN扫出来得到flagflag{ju5t_f0r_FUN}
evilMem
拿到vmem文件先用volatility查一下imageinfo
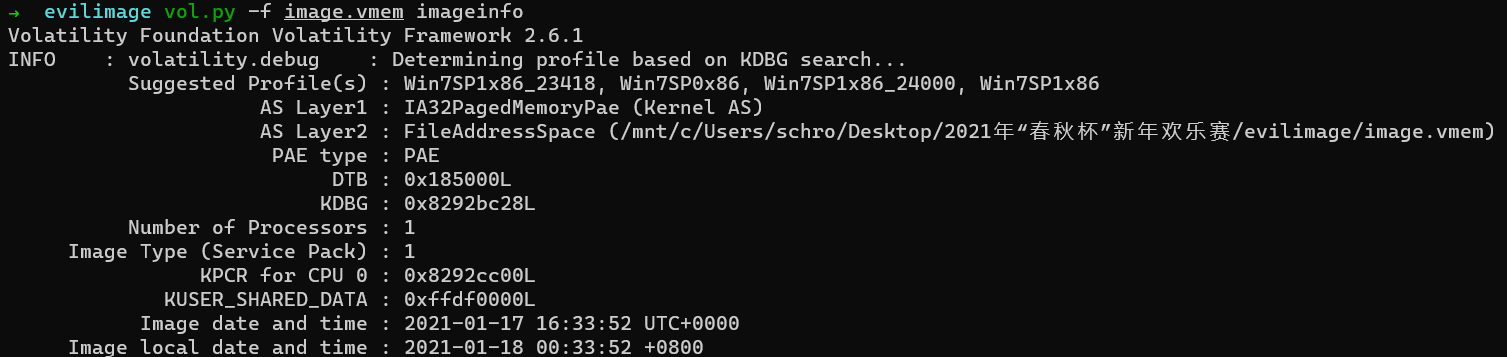
Win7SP1x86
然后查一下进程列表
1 | vol.py -f image.vmem --profile=Win7SP1x86 pslist |
发现进程
1 | 0x858e1030 EvilImage.exe 1884 3516 1 7 1 0 2021-01-17 16:33:41 UTC+0000 |
把进程内存dump出来
1 | vol.py -f image.vmem --profile=Win7SP1x86 memdump -p 1884 -D evilimage/ |
dump出来的内存用foremost恢复一下,恢复出来的文件太多,大多是系统进程,没什么太大的研究价值,根据时间找到两个可疑文件
1 | 28: 00000608.exe 16 KB 311296 01/17/2021 16:28:19 |
修复一下程序segment的raw offset,反编译一下,发现exe文件时主程序EvilImage.exe,dll文件是调用的evil.dll
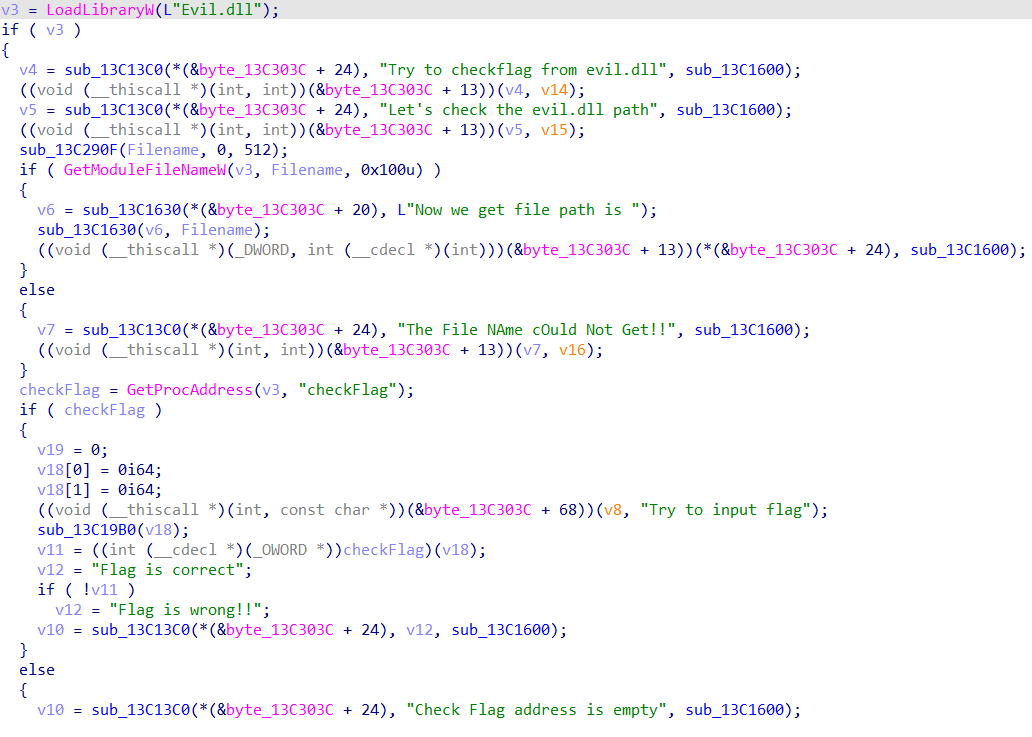
没有修复IAT,但是并不影响理解程序,这里没有太多的内容,只是调用一下Evil.dll里面的checkflag函数判断一下输入的flag是否正确就可以了
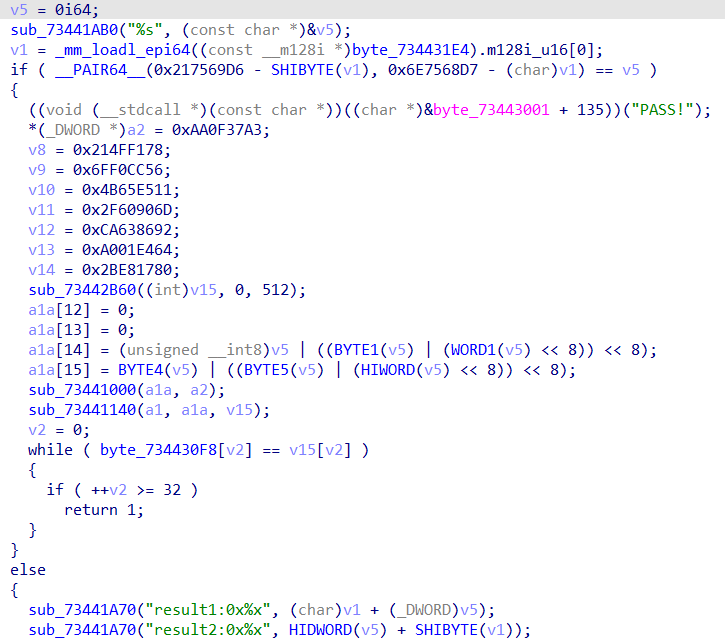
加密过程中出现了很明显的特征“expand 32-byte k”,很容易判断出来是chacha20,v8-v14进行密钥初始化,iv经过if判断条件的计算也可以很轻松地算出来,最后的加密结果也在内存中可以直接读取,解这个密码没有什么难度
1 | import binascii |
十二宫的挑衅
密码本身有点难度,但是因为和zodiac密码的解码方法完全相同,所以只要照着步骤做就很容易解出来
先对密文进行一个简单的换位
1 | s = '''^#@$@#()/>@?==%1( |
然后放到AZdecrypt里面跑一下就出来了
1 | IKILLED A LOT OF PEOPLE AND THE PEOPLE I |
就是flag确实不太好认
snowww
盲水印,binwalk跑出结果有一个matlab脚本,在这里找到讲解和提取水印的脚本
1 | clc;clear;close all; |
跑出结果
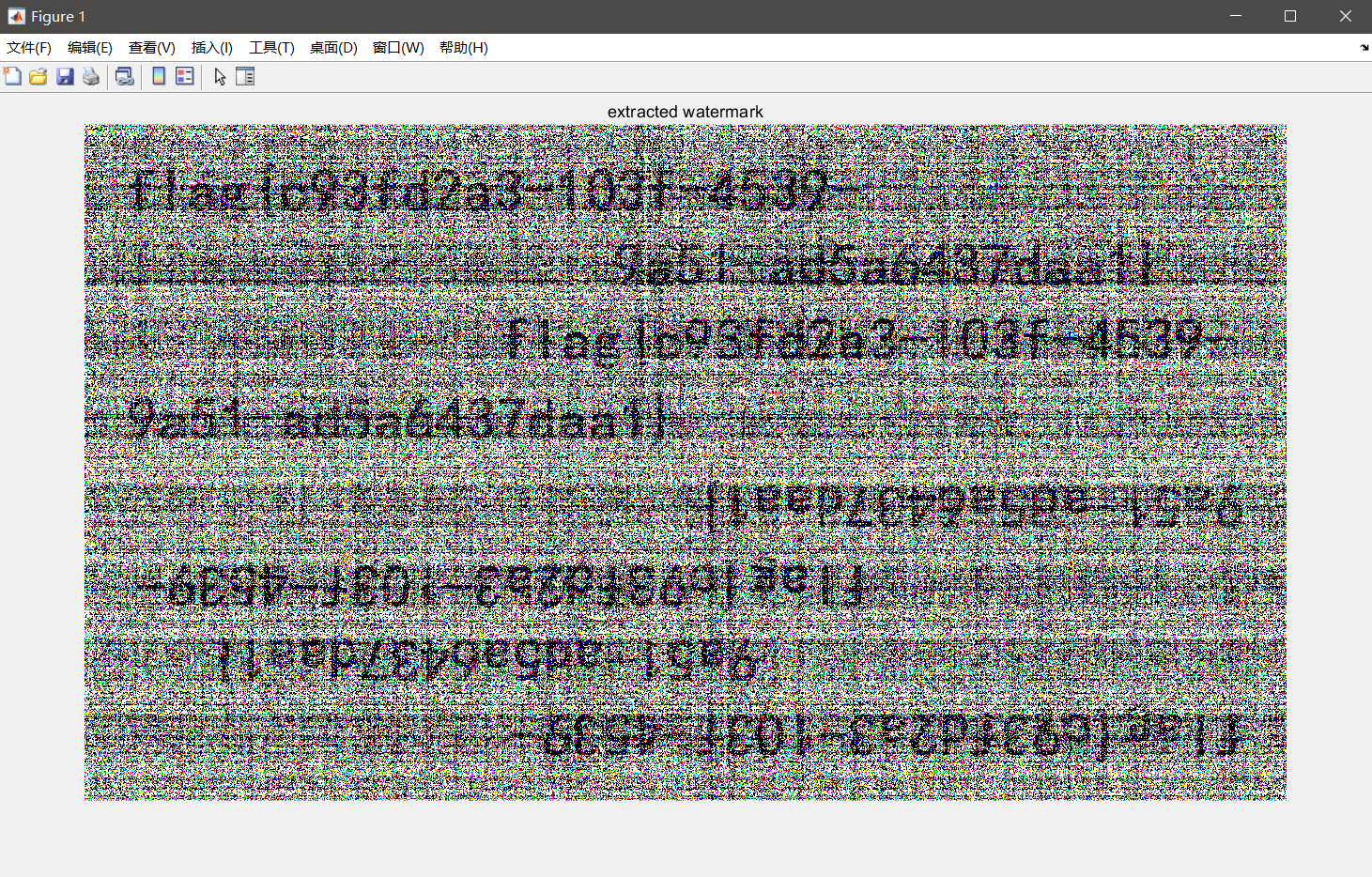
我当时以为这已经是对我眼睛最大的考验了
SuperBrain
似乎是一个开发板的程序,进行一系列初始化之后运行主程序
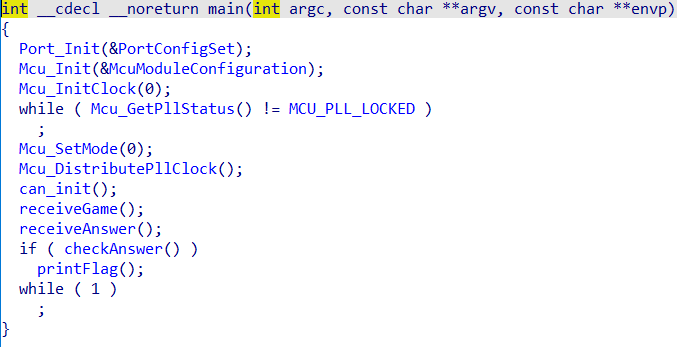
首先会进行通信,接收地图数据和答案数据
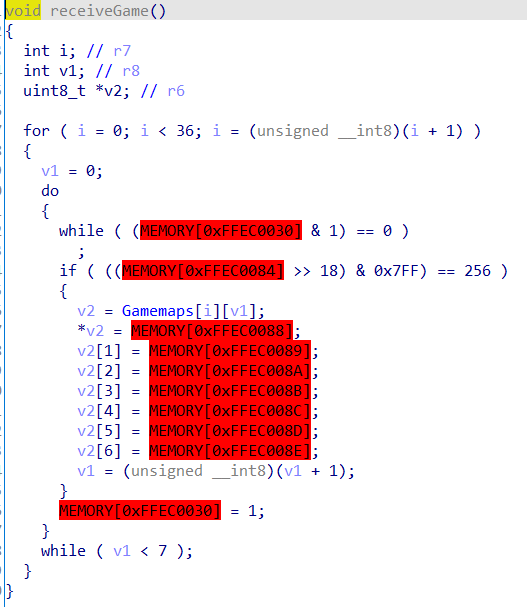
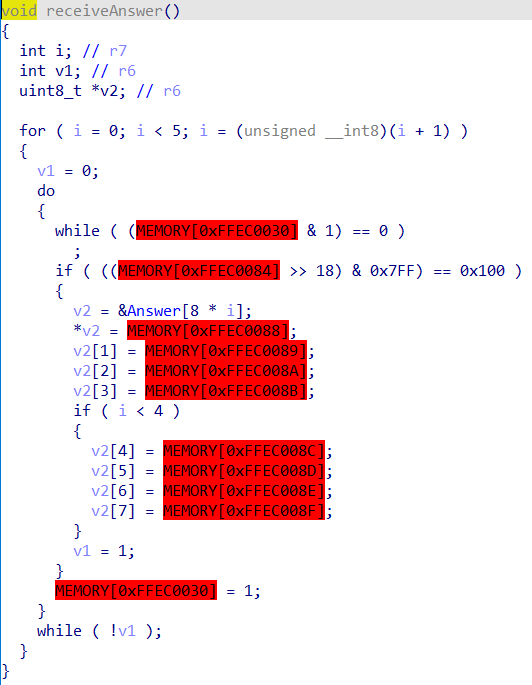
可以看到一共接收了36组地图和36个答案,然后执行程序判断答案是否正确
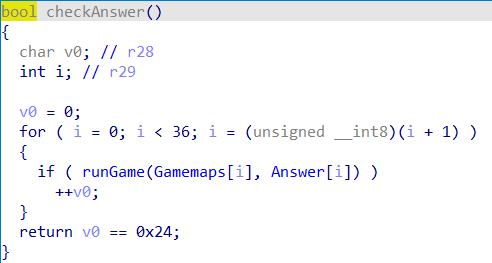
每次执行传入一个地图和对应的答案
执行的程序主要算法如下
1 | answer = (char)answer; |
可以看到类似于走迷宫的算法,分奇偶行执行不同的操作,然后发现答案只传入0-6这7种数字,直接遍历就可以跑出答案
最后一部分输出flag,需要一些数据在内存里都找的到
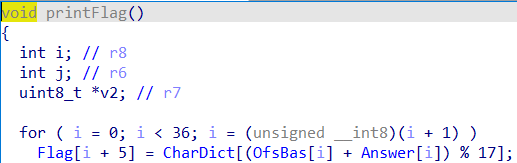
很容易可以解出来
1 | #include <iostream> |
puzzle
每个碎片都加了噪声,还有很多碎片有很大部分重复内容,就算是拼出来图片也看不清楚是什么字符……
但是又太菜了写不出脚本识别,就只能手动拼图+ps识图
1 | flag{w9w45my6x8kk4e8gp9nqm6j2c154wad49} |
2019-nCoV
有三个文件,mp3,wav和一个压缩包,然后题目新增了一个hint,很容易看出来base32编码
1 | http://www.merrybio.com.cn/blog/SARS-CoV-2-genomic-analysis.html |
给的文章有新冠病毒的介绍和基因查询页面,根据提示要算S蛋白质的基因序列的md5得到密码,这个密码是mp3隐写的密码,用MP3Stego解出来又一个密码“2019-nCoV”,试了一下是压缩包密码
1 | m = hashlib.md5() |
wav是lsb隐写,直接用SilentEye解码得到一串没什么意义的字符“priebeijoarkjpxmdkucxwdus”
压缩包得到一张图片和hint2
hint2 16进制转ascii码得到第二个提示
1 | you must pay attention to N protein ,How do that get into the viral capsid? |
图片应该是用steghide做的隐写,隐写的密码是刚刚wav隐写得到的字符经过维吉尼亚密码解码之后的结果,但是维吉尼亚密码的密钥就跟第一句不明不白的话有关系,卡了很久,后来仔细看一下文章,有这么一句话
1 | 核衣壳蛋白(nucleoprotein,N)位于囊膜内部,呈螺旋状,包裹着病毒单股正链的RNA基因组。病毒在进行装配时,N蛋白先和病毒RNA相互作用形成复合体形式,然后再结合M蛋白、E蛋白,最后被包装进入病毒衣壳内。 |
猜测是对N蛋白质、M蛋白质、E蛋白质的基因序列进行词频统计
1 | dic = {} |
一共20个字符按照频次从高到低的顺序排列,在后面添加COMBAT得到密钥LGASTRIQKNDPFEVYMWHCCOMBAT
解维吉尼亚密码得到隐写的密码eliminatenovelcoronavirts
用steghide解出flag
1 | flag{we_will_over_come_SARS-COV} |
Comments