Javis OJ的题目还是很不错的,可以仔细研究研究
re
Findkey
DIE看看发现是pyc文件,试一下uncompyle6发现直接成功没加任何保护,看看代码
1 | import sys |
简单写个脚本逆一下
1 | lookup = [ |
Classical Crackme
这题有confuser的混淆,想脱掉这个壳有点困难,所以先看看代码
1 | private void \u202C\u200B\u206A\u202A\u206D\u206B\u202D\u206F\u202D\u200C\u200E\u206B\u202E\u202E\u202C\u202B\u206A\u206D\u206E\u202B\u206E\u200F\u202D\u200E\u202C\u200F\u200D\u200F\u202B\u200C\u202A\u206D\u206A\u206E\u202D\u200D\u200C\u206B\u202A\u202D\u202E(object A_1, EventArgs A_2) |
找到关键部分,发现是简单对输入base64处理,然后直接对比,所以base64解码之后就可以了
Classic Crackme2
这题和上一个基本相似,也是c#+confuser,不过这次想直接找到关键代码有点困难,所以调试解决,在主函数下断点
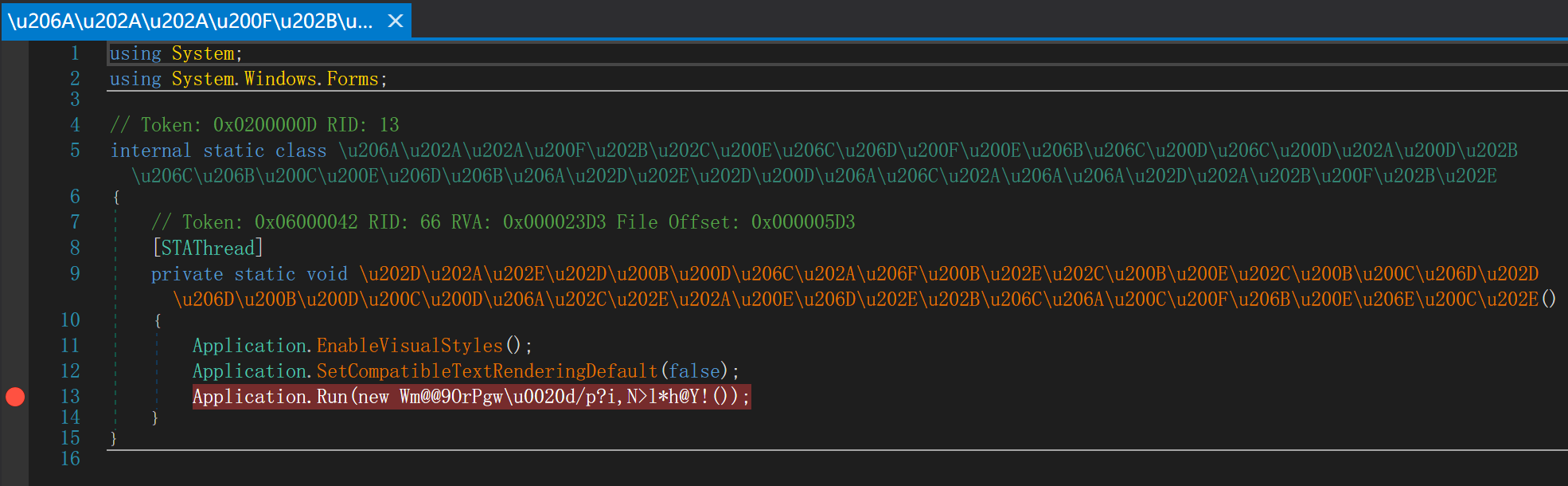
断点处这一串奇怪的字符串名应该就是关键的类,启动调试,跟进去
调试过程中发现了关键的比较
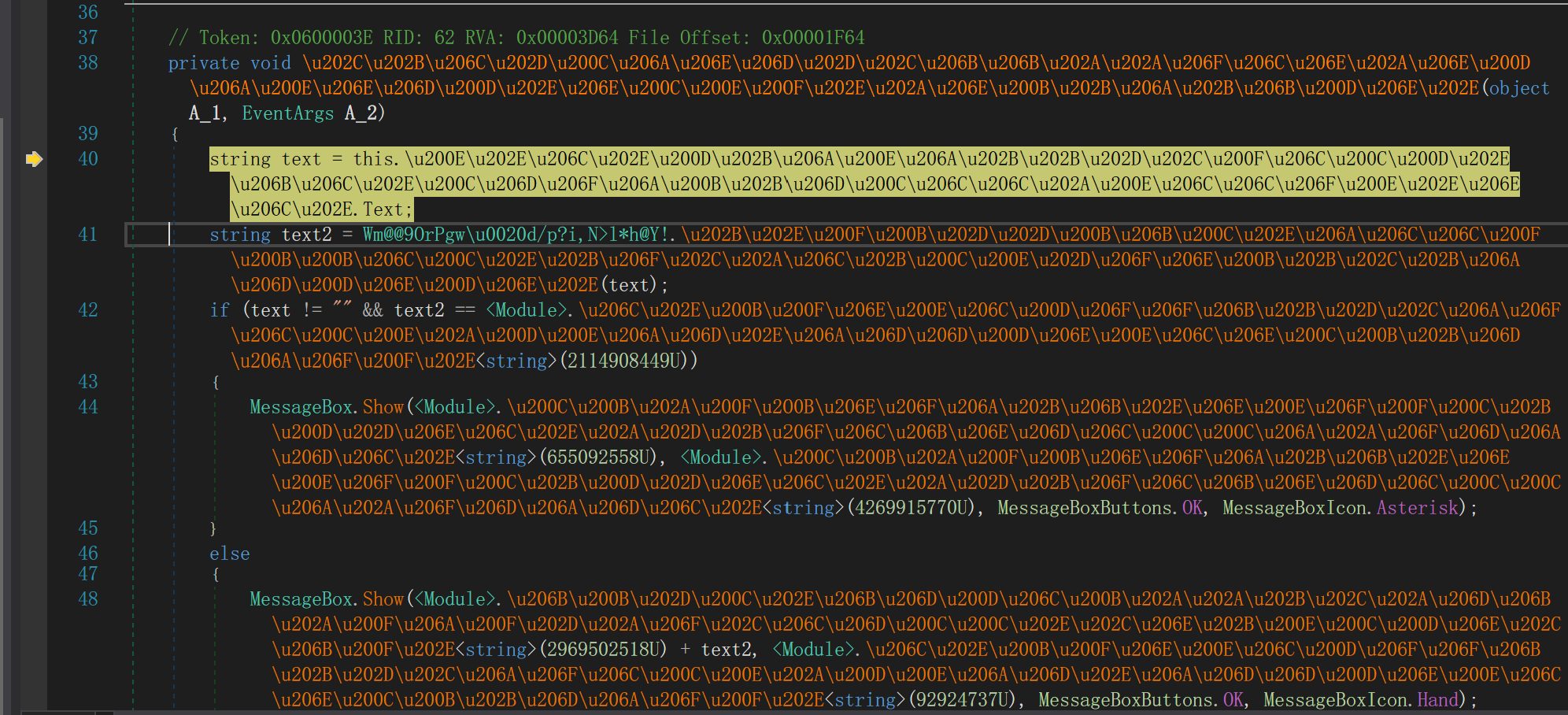
text1是我们的输入,去看看text2是什么
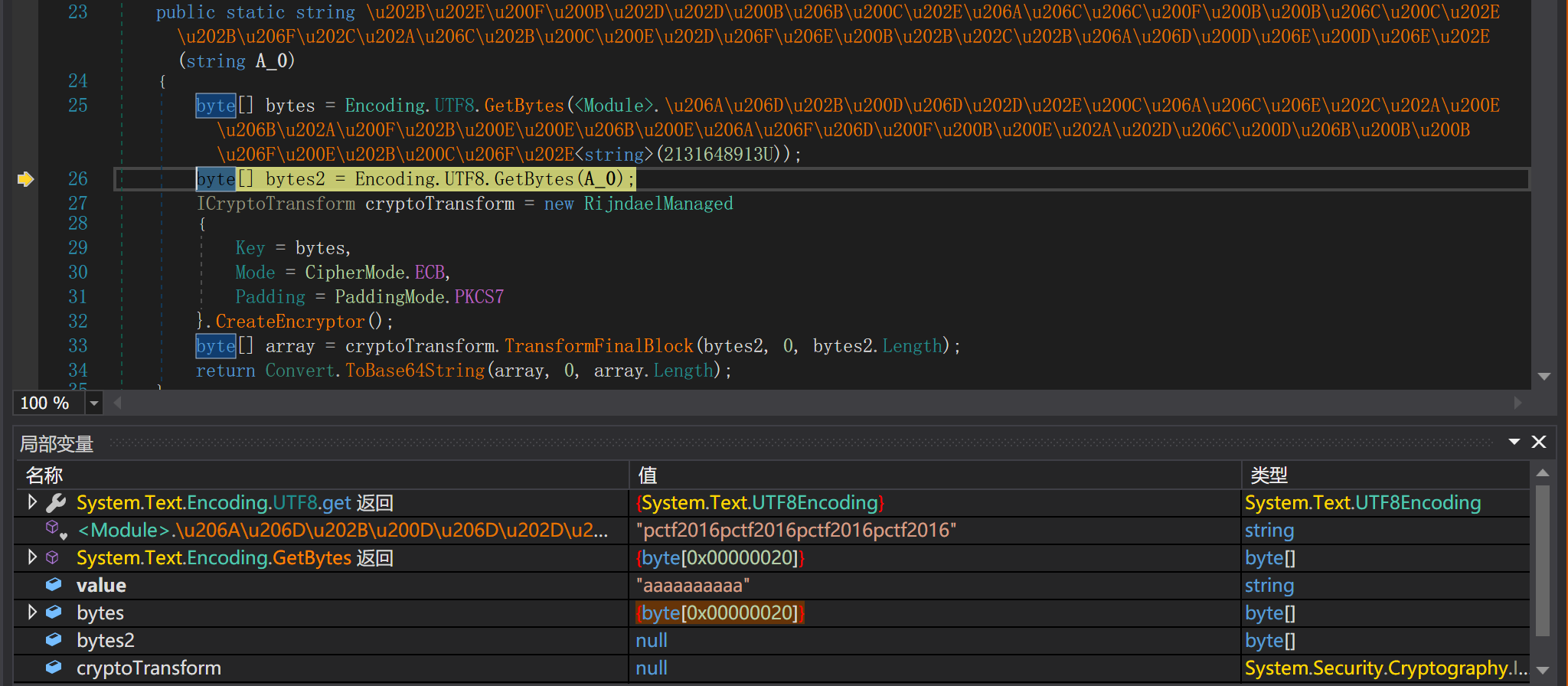
发现加密方式是AES-ECB方式加密,填充方式也已知,key在局部变量窗口可以获得,最后应该还有个比较,接着调试
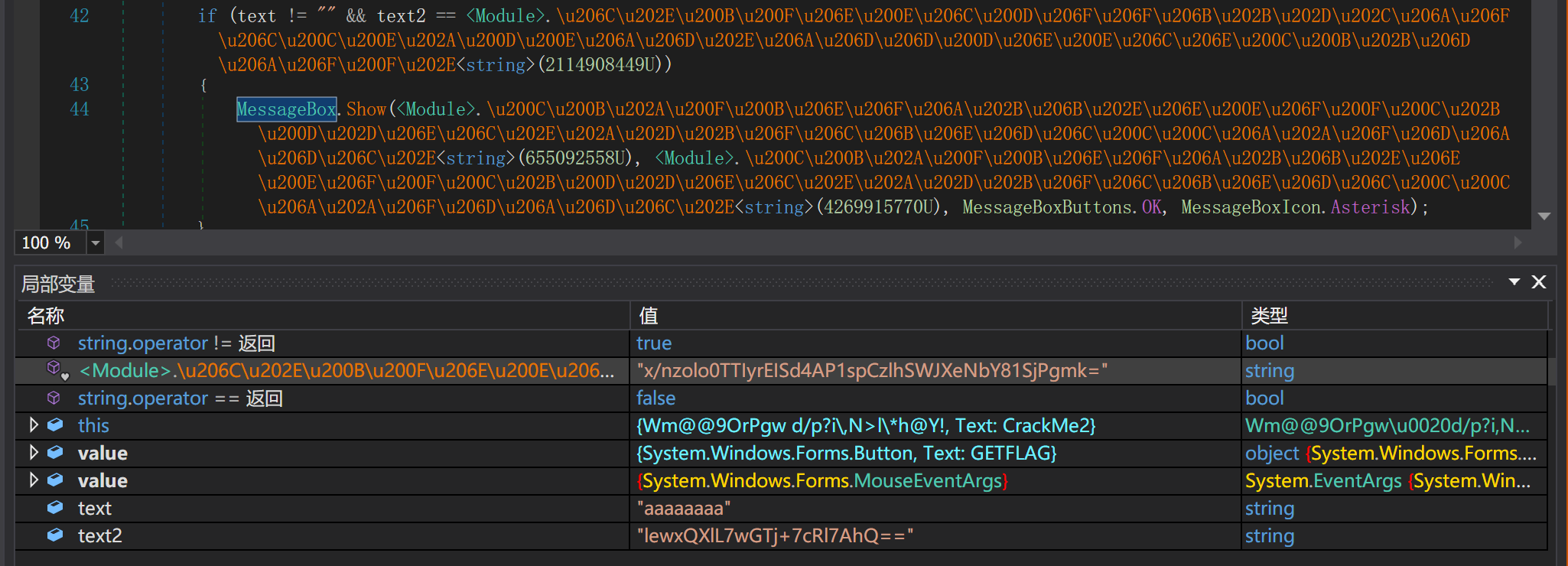
发现了我们的输入被加密之后和另一串进行了一个比较,然后就可以写个脚本来跑一跑
1 | import base64 |
Smali
Smali的语法我还是不是很会,不过这题比较简单,可以很容易看出来,也是简单的AES加密
1 | import base64 |
Comments