1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
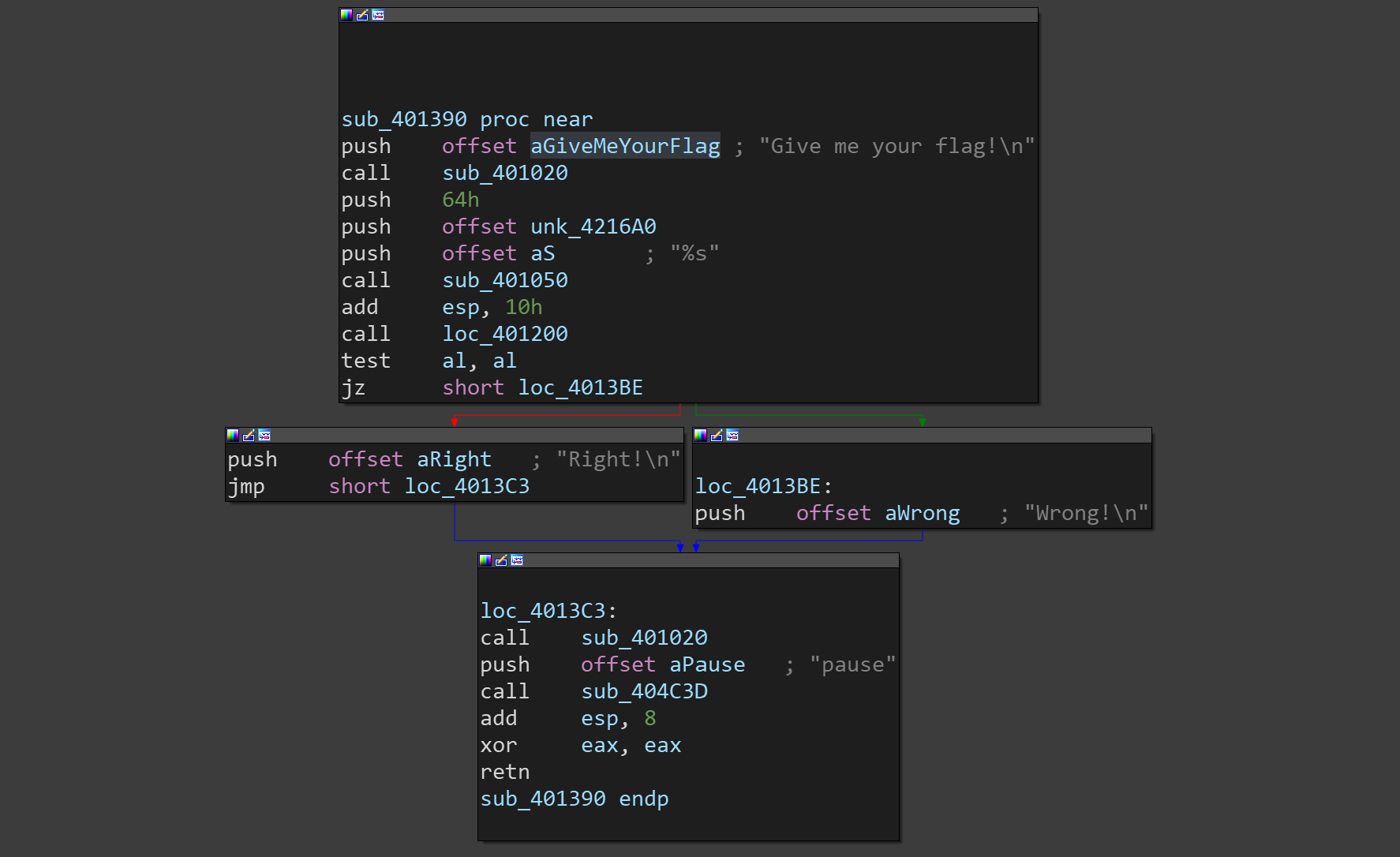
| loc_40127B: ; CODE XREF: .text:00401273↑j
.text:0040127B xor eax, eax
.text:0040127D jz short loc_401280
.text:0040127D ; ---------------------------------------------------------------------------
.text:0040127F db 0E8h
.text:00401280 ; ---------------------------------------------------------------------------
.text:00401280
.text:00401280 loc_401280: ; CODE XREF: .text:0040127D↑j
.text:00401280 xor esi, esi
.text:00401282 mov esi, 2Bh
.text:00401287
.text:00401287 loc_401287: ; CODE XREF: .text:004012AF↓j
.text:00401287 xor eax, eax
.text:00401289 mov al, byte ptr (dword_42169C+3)[esi]
.text:0040128F mov ecx, esi
.text:00401291 xor ebx, ebx
.text:00401293 jz short loc_401296
.text:00401293 ; ---------------------------------------------------------------------------
.text:00401295 db 0E8h
.text:00401296 ; ---------------------------------------------------------------------------
.text:00401296
.text:00401296 loc_401296: ; CODE XREF: .text:00401293↑j
.text:00401296 and ecx, 1
.text:00401299 cmp ecx, 0
.text:0040129C jz short loc_4012A3
.text:0040129E ror al, 4
.text:004012A1 jmp short loc_4012A6
.text:004012A3 ; ---------------------------------------------------------------------------
.text:004012A3
.text:004012A3 loc_4012A3: ; CODE XREF: .text:0040129C↑j
.text:004012A3 rol al, 4
.text:004012A6
.text:004012A6 loc_4012A6: ; CODE XREF: .text:004012A1↑j
.text:004012A6 mov byte ptr (dword_42169C+3)[esi], al
.text:004012AC dec esi
.text:004012AD test esi, esi
.text:004012AF jnz short loc_401287
.text:004012B1 mov edx, 2Bh
.text:004012B6 mov ecx, offset unk_4216A0
.text:004012BB call sub_401090
.text:004012C0 mov dword ptr [ebp-0Ch], offset byte_421708
.text:004012C7 mov edx, [ebp-0Ch]
.text:004012CA add edx, 1
.text:004012CD mov [ebp-28h], edx
.text:004012D0
.text:004012D0 loc_4012D0: ; CODE XREF: .text:004012E0↓j
.text:004012D0 mov eax, [ebp-0Ch]
.text:004012D3 mov cl, [eax]
.text:004012D5 mov [ebp-2], cl
.text:004012D8 add dword ptr [ebp-0Ch], 1
.text:004012DC cmp byte ptr [ebp-2], 0
.text:004012E0 jnz short loc_4012D0
.text:004012E2 mov edx, [ebp-0Ch]
.text:004012E5 sub edx, [ebp-28h]
.text:004012E8 mov [ebp-30h], edx
.text:004012EB mov dword ptr [ebp-10h], offset aBuedvshlmfwhpz ; "%BUEdVSHlmfWhpZn!oaWZ(aGBsZ@ZpZn!oaWZ(a"...
.text:004012F2 mov eax, [ebp-10h]
.text:004012F5 add eax, 1
.text:004012F8 mov [ebp-2Ch], eax
.text:004012FB
.text:004012FB loc_4012FB: ; CODE XREF: .text:0040130B↓j
.text:004012FB mov ecx, [ebp-10h]
.text:004012FE mov dl, [ecx]
.text:00401300 mov [ebp-3], dl
.text:00401303 add dword ptr [ebp-10h], 1
.text:00401307 cmp byte ptr [ebp-3], 0
.text:0040130B jnz short loc_4012FB
.text:0040130D mov eax, [ebp-10h]
.text:00401310 sub eax, [ebp-2Ch]
.text:00401313 mov [ebp-34h], eax
.text:00401316 mov ecx, [ebp-30h]
.text:00401319 cmp ecx, [ebp-34h]
.text:0040131C jz short loc_401322
.text:0040131E xor al, al
.text:00401320 jmp short loc_401387
.text:00401322 ; ---------------------------------------------------------------------------
.text:00401322
.text:00401322 loc_401322: ; CODE XREF: .text:0040131C↑j
.text:00401322 mov dword ptr [ebp-18h], 0
.text:00401329 jmp short loc_401334
.text:0040132B ; ---------------------------------------------------------------------------
.text:0040132B
.text:0040132B loc_40132B: ; CODE XREF: .text:loc_401383↓j
.text:0040132B mov edx, [ebp-18h]
.text:0040132E add edx, 1
.text:00401331 mov [ebp-18h], edx
.text:00401334
.text:00401334 loc_401334: ; CODE XREF: .text:00401329↑j
.text:00401334 mov dword ptr [ebp-14h], offset byte_421708
.text:0040133B mov eax, [ebp-14h]
.text:0040133E add eax, 1
.text:00401341 mov [ebp-38h], eax
.text:00401344
.text:00401344 loc_401344: ; CODE XREF: .text:00401354↓j
.text:00401344 mov ecx, [ebp-14h]
.text:00401347 mov dl, [ecx]
.text:00401349 mov [ebp-4], dl
.text:0040134C add dword ptr [ebp-14h], 1
.text:00401350 cmp byte ptr [ebp-4], 0
.text:00401354 jnz short loc_401344
.text:00401356 mov eax, [ebp-14h]
.text:00401359 sub eax, [ebp-38h]
.text:0040135C mov [ebp-3Ch], eax
.text:0040135F mov ecx, [ebp-18h]
.text:00401362 cmp ecx, [ebp-3Ch]
.text:00401365 jnb short loc_401385
.text:00401367 mov edx, [ebp-18h]
.text:0040136A movsx eax, byte_421708[edx]
.text:00401371 mov ecx, [ebp-18h]
.text:00401374 movsx edx, byte ptr aBuedvshlmfwhpz[ecx] ; "%BUEdVSHlmfWhpZn!oaWZ(aGBsZ@ZpZn!oaWZ(a"...
.text:0040137B cmp eax, edx
.text:0040137D jz short loc_401383
.text:0040137F xor al, al
.text:00401381 jmp short loc_401387
.text:00401383 ; ---------------------------------------------------------------------------
.text:00401383
.text:00401383 loc_401383: ; CODE XREF: .text:0040137D↑j
.text:00401383 jmp short loc_40132B
.text:00401385 ; ---------------------------------------------------------------------------
.text:00401385
.text:00401385 loc_401385: ; CODE XREF: .text:00401365↑j
.text:00401385 mov al, 1
.text:00401387
.text:00401387 loc_401387: ; CODE XREF: .text:0040124C↑j
.text:00401387 ; .text:00401320↑j ...
.text:00401387 pop edi
.text:00401388 pop esi
.text:00401389 pop ebx
.text:0040138A mov esp, ebp
.text:0040138C pop ebp
.text:0040138D retn
|
Comments